Two-Factor Authentication on the EO-Lab Site Using a Mobile Application
This guide explains how to enable and use two-factor authentication (2FA) on the EO-Lab site using mobile apps such as FreeOTP. By following this tutorial, you’ll secure your account with Time-based One-Time Passwords (TOTP) generated on your smartphone.
What We Are Going to Cover
Introduction to Two-Factor Authentication (2FA)
Traditionally, online security relied on a combination of usernames and passwords. Most usernames are email addresses, and if an email address is breached, attackers may easily guess or retrieve the password too. Brute-force methods, cloud computing power, social engineering, and identity theft have made password-only systems increasingly vulnerable.
To counteract this, modern systems use two or more factors of authentication:
Something the user knows — e.g., a password or a security question.
Something the user has — e.g., a smartphone, token, or smart card.
Something the user is — e.g., biometric data like fingerprint or face scan.
On EO-Lab, two-factor authentication (2FA) requires:
Your username and password
A TOTP code generated by a mobile app
This article explains how to use a mobile device for 2FA. To use your computer for the same purpose, see: Two-Factor Authentication to EO-Lab site using KeePassXC on desktop.
We’ll refer to “mobile authenticator” as a generic term for any 2FA mobile app.
Authenticator App Comparison
Feature |
FreeOTP |
Google Authenticator |
Microsoft Authenticator |
|---|---|---|---|
Developer |
Red Hat |
Microsoft |
|
Cost |
Free |
Free |
Free |
Open Source |
Yes |
No |
No |
2FA Method |
TOTP, HOTP |
TOTP |
TOTP, Push Notifications, Passwordless |
Cloud Backup |
No |
No |
Yes (encrypted) |
Push Notifications |
No |
No |
Yes (for Microsoft accounts) |
Account Transfer |
QR code export only |
QR code export |
Cloud sync |
Customization |
Limited |
Limited |
Rich naming, icons |
Integration |
Broad (TOTP/HOTP) |
TOTP only |
Best with Microsoft ecosystem |
Security |
High (offline, open-source) |
High (offline) |
High (biometric lock) |
Biometric Lock |
No |
No |
Yes |
Multi-Device Sync |
No |
No |
Yes |
Usability |
Minimalist |
Simple |
Feature-rich |
You can use FreeOTP for Google accounts too. If you already use Google Authenticator, you may prefer to stick with it.
Common Issues with Mobile Authenticators
Caution
Losing your mobile device without recovery codes may lock you out permanently.
- FreeOTP
No backup or sync
Manual reconfiguration for each account
- Google Authenticator
No cloud backup
Vulnerable if phone/SMS is lost
- Microsoft Authenticator
Best with Microsoft accounts
Cloud sync requires Microsoft account
In this tutorial, we’ll use FreeOTP.
Warning
If you lose access to QR codes or the mobile device, email support@cloudferro.com for recovery assistance.
Prerequisites
Account
You need a valid hosting account with Horizon access: https://cloud.fra1-1.cloudferro.com/auth/login/?next=/.
Authenticator App on Your Phone
App |
FreeOTP |
Google Authenticator |
Microsoft Authenticator |
|---|---|---|---|
Platforms |
Install the app according to your device’s platform guidelines.
Setting Up the Secret Code
Note
Setup is usually performed once; however, you’ll need to use the mobile app every time you log in.
The 2FA process relies on a shared secret — a 32-character base32 string used to generate TOTP codes.
There are two setup methods:
Scan a QR code — easier, but doesn’t reveal the secret.
Enter the secret manually — useful for automation or backups.
To begin setup:
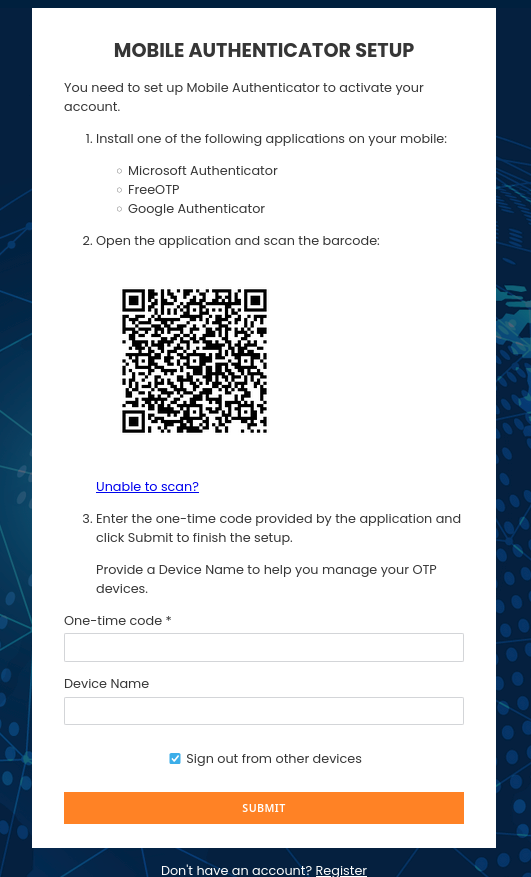
|
|
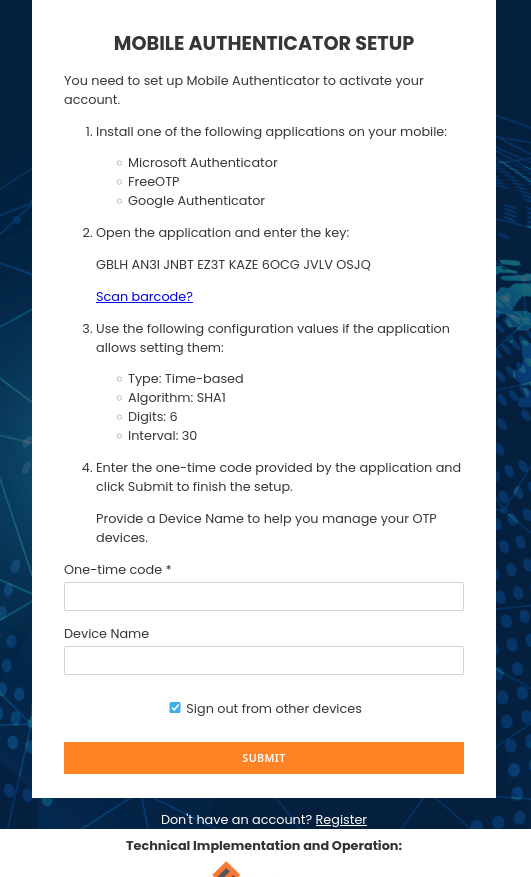
Click Unable to scan? to reveal the secret string.
Option 1: Scan the QR Code
Open FreeOTP
Tap the plus (+) icon → tap QR code icon
Scan the QR code
A new TOTP entry will appear
Note
Every page reload generates a new QR/secret — use it immediately or save securely.
Option 2: Enter the Secret Manually
Copy the key (e.g., GBLH AN3I JNBT EZ3T KAZE 6OCG JVLV OSJQ) and enter the values:
Type: TOTP
Algorithm: SHA1
Digits: 6
Interval: 30 seconds
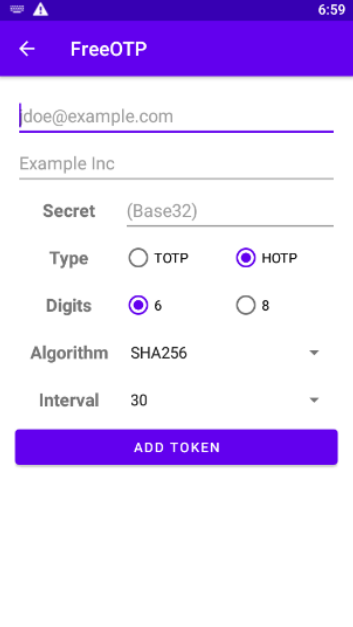
Replace jdoe@example.com and Example Inc with your details.
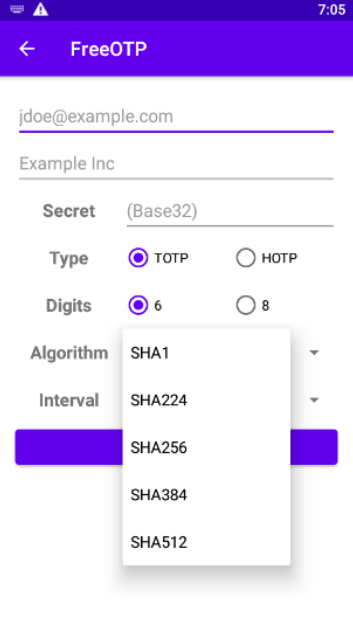
Tap ADD TOKEN to save the entry.
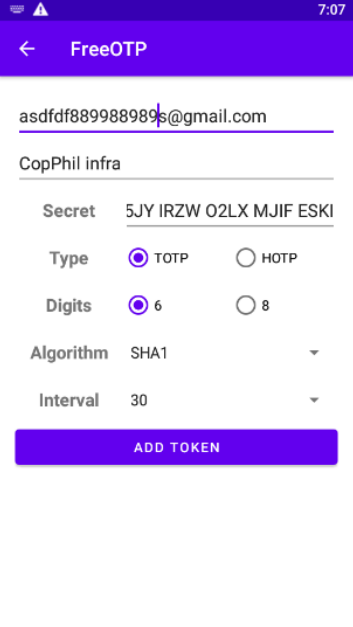
To get your 6-digit code, tap the entry:

Logging Into the Dashboard with 2FA
Select EO-Lab from the drop-down
Click Sign In
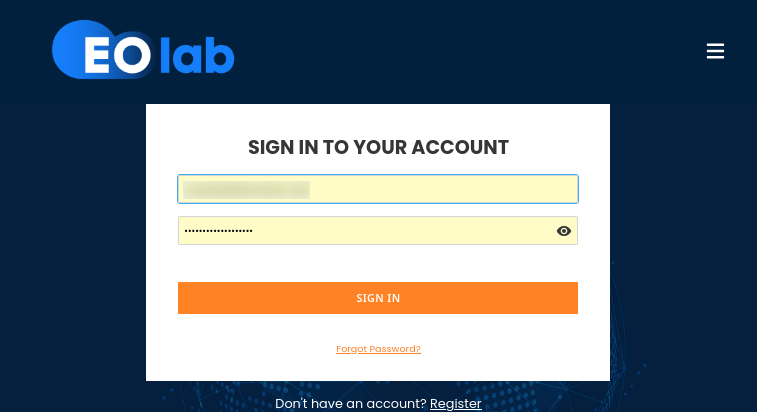
Enter your TOTP code
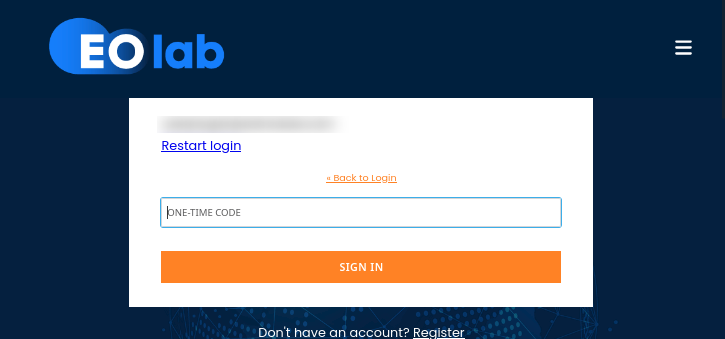
Open FreeOTP, get the code, and submit.
Note
FreeOTP may auto-generate the code when it’s running in foreground.
Logging Into Horizon
Two ways:
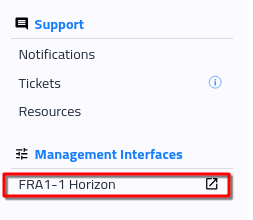
Method 1: From Dashboard
Click on link FRA1-1 Horizon in the dashboard:
Method 2: Direct Link
Visit https://cloud.fra1-1.cloudferro.com/auth/login/?next=/ directly. You’ll be prompted to re-enter your 2FA code.
Either way, you get to this form:
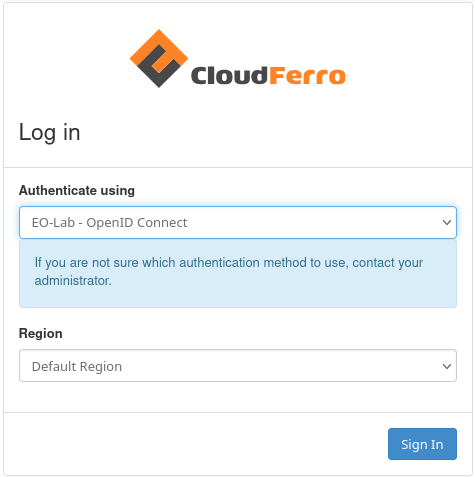
Authenticate and enter the OpenStack Horizon interface:
What To Do Next
To use your computer for 2FA, see: Two-Factor Authentication to EO-Lab site using KeePassXC on desktop.
After logging in, you can activate OpenStack CLI access with your 2FA-enabled account: How to Activate OpenStack CLI Access to EO-Lab Cloud Using One- or Two-Factor Authentication