Generating an SSH keypair in Linux on EO-Lab
In order to generate an SSH keypair in Linux, we recommend using the command ssh-keygen. If your system doesn’t have this package installed, please install the latest version with:
sudo apt-get update && apt-get install openssh-client
for Ubuntu and Debian family, or
sudo yum install openssh-clients
for CentOS and Red Hat.
Using ssh-keygen with default parameters
Issue the following command:
ssh-keygen
in systems terminal. For all entry points, answer by pressing Enter on the keyboard. ssh-keygen will then use the default values. This is a typical result:
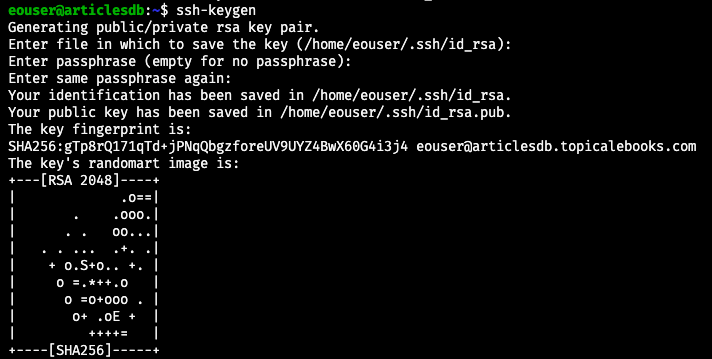
The command will ask for the following data:
file in which to save the secret key – default is /.ssh/id_rsa
file in which to save the public key – default is /.ssh.id_rsa.pug
It will print key fingerprint and append user and server name at the end, to make it more unique.
The last piece of output is quasi-graphic image to symbolically show that the keys were generated in a random fashion.
Using ssh-keygen with specific parameters
The full list of parameters for ssh-keygen will be shown after
ssh-keygen --help
The following image shows the result:
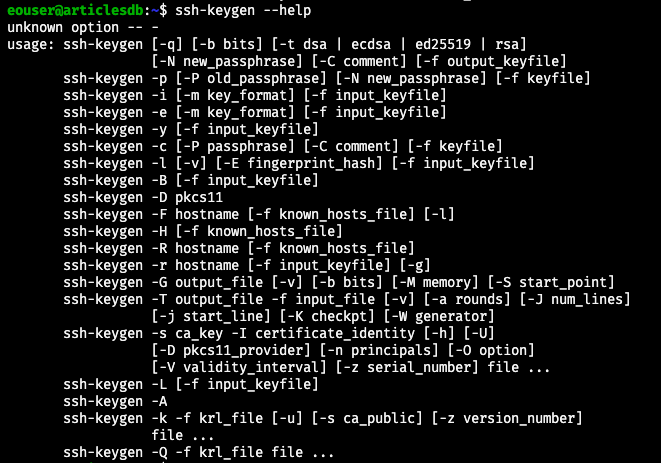
Here are the most important parameters to consider:
Authentication key type
Parameter is -t and possible values are dsa, ecdsa, ed25519, rsa
Bit length
Parameter is -b and defines bit length. The greater the value, the more complicated the key will be. Available values: 1024, 2048, 4096; 2048 is the default.
Identification at the end of the file
Parameter is -C and the value is of type user@server; it will be appended to the end of keys value.
Passphrase
Parameter is -N. Can be ommited if user prefers connecting without additional key security.
Example of ssh-keygen command with parameters
Let us use the following command to generate public and private keys:
ssh-keygen -t rsa -b 1024 -C "user@youruser.com" -N fejdferereede
Now there is a bit of a difference: file id_rsa already exists from the previous command without parameters so in this example we call that file id_rsa1:
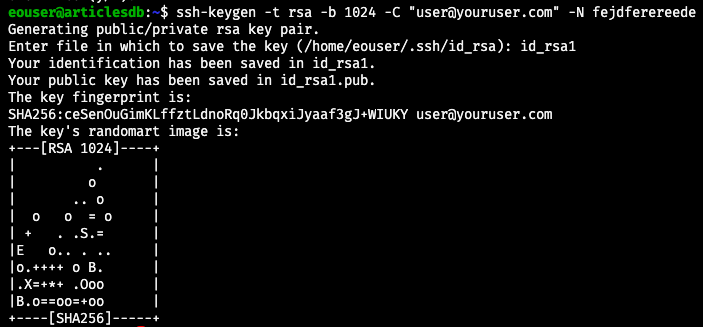
We also see that the quasi-random graphics at the end is different compared to the the same graphic with default parameters of ssh-keygen.
Implement additional security for public and private keys
The keys can be a very strong guarantee of safety, which is especially important in server and remote communications. Therefore, the files in which they reside should not be easily changed or executed in any way. To change their permissions, navigate to the folder containing both keys and enter command:
chmod 600 id_rsa && chmod 600 id_rsa.pub
Permission 600 means that only the owner of the file has full read and write access to it. Once a file permission is set to 600, no one else can access the file.
You can even use permission 400, which means that the user can read the value of the file but can neither execute it nor write to it.